IS-IS was developed for routing ISO CLNP networks and operates in strictly ISO CLNS terms; while
Integrated IS-IS is an implementation of IS-IS that supports both ISO CLNS and IP in a single protocol. Integrated IS-IS tags CLNP routes with information about IP subnets. Integrated IS-IS provides an alternative to the dominant OSPF. It can be used for CLNS routing, IP routing, or a combination of both. CLNP is the first routed protocol for which IS-IS has provided routing services; the support for IP was added later.
IS-IS is a public standard that was originally published as ISO 10589 and republished as
RFC 1142 – OSI IS-IS Intra-domain Routing Protocol; while Integrated IS-IS (or Dual IS-IS) is published as
RFC 1195 – Use of OSI IS-IS for Routing in TCP/IP and Dual Environments.
CLNS addresses apply to entire nodes and not to interfaces. Since IS-IS was originally designed for CLNS and IS-IS
Link-State PDUs (LSPs) use NSAP addresses to identify the router, build the link-state topology table and the underlying IS-IS routing tree; therefore Integrated IS-IS still requires CLNS NSAP node addresses to function properly, even when it is being implemented for IP routing only on a router that is forwarding only IP packets.
OSPF runs on top of IP; IS-IS runs directly on top of the data link layer –
protocol independent.
Integrated IS-IS supports VLSM and provides fast convergence ability as like OSPF and EIGRP. Each of them has its advantages and disadvantages, but this communality makes any of them scalable and appropriate for supporting today’s large-scale networks.
IS-IS operates similarly to OSPF. IS-IS allows a routing domain to be partitioned into areas. IS-IS routers establish adjacencies using a Hello mechanism and exchange link-state information using Link-State PDUs (LSPs) through an area to build the link-state topology database (LSDB). Every IS-IS router then applies Dijkstra’s SPF algorithm upon its LSDB to build the SPF tree –
SPT and select the best paths to be installed into the routing table. There is a minimal amount of info communicated between areas compared to OSPF, which reduces the burden of IS-IS routers. IS-IS could be described as
OSPF using only totally-stubby areas.
As with other LS routing protocols, IS-IS routers have the full picture of the network topology, and can independently make routing decisions based on the accurate picture of the network.
IS-IS takes place at 2 levels within a routing domain –
Level 1 (L1) and
Level 2 (L2).
L1 routing occurs within an IS-IS area and is responsible for routing ESs and ISs inside an area (intra-area routing). All devices in an L1 routing area have the same area address. Routing within an area is accomplished using the locally significant address portion known as the System ID, and choosing the lowest-cost path. L1 builds a topology of System IDs in the local area and routes traffic
within the area using the lowest-cost paths.
L2 routing occurs between IS-IS areas (inter-area routing). L2 routers learn the locations of L1 routing areas to build the inter-area topology and routing table. L2 routers use the destination area address to route traffic using the lowest-cost paths. L2 exchanges prefix information (area addresses) between areas and routes traffic
between areas using the lowest-cost paths.
Note: Level 0 (L0) routing occurs between ESs and ISs on the same subnet. The OSI routing process begins at this level – end system and intermediate system. Level 3 (L3) routing occurs between separate OSI routing domains using IDRP; similar to BGP in IP inter-domain routing.
3 Types of IS-IS Routers
IS-IS defines 3 types of routers to support the 2-level L1 and L2 hierarchical routing:
- L1 routers use LSPs to learn about paths within the areas they reside in (intra-area). They form adjacencies and exchange routing info amongst themselves within an L1 area. It is similar to an OSPF totally stub router, which has only the topological info of an area, and uses a default route to the nearest L1/L2 router to route traffic to other areas.
- L2 routers use LSPs to learn about paths between areas they reside in (inter-area). They are considered backbone routers that only form adjacencies and exchange routing info amongst themselves within the backbone and route traffic between areas.
- Level 1 / Level 2 (L1/L2) combo routers learn about paths both within and between areas. They allow the L1- and L2-only routers to exchange routing information between areas. L1/L2 routers are equivalent to area border routers (ABRs) in OSPF. An L1/L2 router maintains a L1 LSDB for the area that it resides in and a L2 LSDB for inter-area routing.
IP subnets are treated as leafs in the IS-IS SPT. Areas as recognized by the format of their NETs produce a summary into L2, and the L1/L2 router inject a default route back into L1 areas.
Designing a totally flat IS-IS network with all L1/L2 routers provides an advantage of easy migration to multiple areas.
An IS-IS router may reside in a L1 area, in the L2 backbone, or both. L1/L2 routers connect L1 areas to the L2 backbone. An L1/L2 router will maintain a L1 routing table to route to ES and IS within its own area using System IDs, and a L2 prefix table to route to other areas. When the only L1/L2 router in an area failed, the area would be unreachable throughout the routing domain!
An L2 router is similar to an OSPF backbone router. The paths between the L2 and L1/L2 routers are called the backbone. All L2 and L1/L2 routers (the path of the backbone) must be contiguous – they cannot be separated by a L1 router somewhere in the middle.
An IS-IS router normally has 1 NET address. The limit is 3 NETs for conventional IS-IS; and 3 NETs per area for multiarea Integrated IS-IS. Configuring multiple NETs on routers is a useful technique for merging 2 domains or transitioning from one addressing scheme to another. If multiple NETs are configured on the same router, they all must have the same System ID. The default can be changed using the
max-area-addresses router subcommand.
Note: The wording of
area in this context is more appropriate being referred to as
process.
Area Boundaries of OSPF and IS-IS
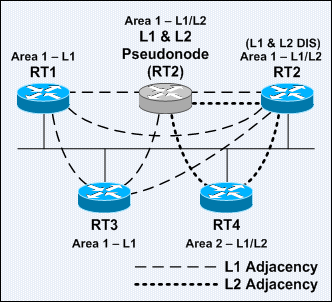
IS-IS area boundaries lie on links instead of routers as with OSPF. Each IS-IS router belongs to exactly one area. Neighboring routers are able to learn that they are in the same or different areas and negotiate the appropriate adjacencies – L1, L2, or both.
[Integrated] IS-IS has its own
Protocol Data Units (PDUs) to transport information between ISs. Conventional IS-IS and Integrated IS-IS routing information is not carried within a network layer routed protocol (eg: CLNP) but is instead encapsulated directly within data link layer frames.
With OSPF, network design is constrained because OSPF is based on a central backbone area 0, with the restriction that all other areas must be physically or logically connected to backbone. In comparison, IS-IS has a hierarchy of L1, L1/L2, and L2 routers. IS-IS permits a more flexible approach upon extending the backbone. The backbone can be extended by simply adding additional L1/L2 or L2 routers, a much less-complex process than with OSPF.
OSPF generates many types of small LSAs; whereas IS-IS groups IS-IS updates and sends them in a single LSP. As the network complexity increases, flooding of IS-IS updates is not an issue. Since each packet must be routed though, and routing takes network resources, so more packets represent a larger impact on the network. Since IS-IS uses significantly fewer LSPs, more routers, at least 1000, can reside in a single area, making IS-IS more scalable than OSPF.
IS-IS and OSPF Routing Updates
IS-IS is also more efficient than OSPF in terms of CPU usages and processing routing updates. There are fewer LSPs (LSAs in OSPF terminology) to process. Besides that, the mechanism by which IS-IS installs and withdraws prefixes is less resource intensive as it uses NET addresses, which are already summarized.
The convergence time depends on various factors, eg: timers, number of nodes, and router type. Based on the default times, IS-IS detects a failure faster than OSPF; therefore faster convergence. IS-IS has more timers than OSPF for fine-tuning and achieve finer granularity. Convergence time can be decreased significantly by fine-tuning those timers.
L1/L2 routers should implement route summarization. Route summarization has many benefits. It saves CPU and memory resources since every router no longer responsible for the LSPs of the entire routing domain, and topology changes can be isolated to a small portion of the network instead of be propagating throughout the entire domain; therefore routers in other portions of the network can spend lesser time and resources for routing convergence upon topology changes.
Below lists the rules for implementing route summarization on IS-IS:
- All L2 routers can summarize routes at the area boundary.
- When an L1/L2 router is summarizing routes sent to an L2 router, all L1/L2 routers must summarize in the same way.
- All L1 routers cannot summarize routes.
Older implementations of IS-IS use
narrow metrics, which limits the maximum interface metric to 63 (6-bit) and the maximum total path metric to 1023 (10-bit); hence provides little space to distinguish between paths. Cisco IOS Software Release 12.0 and later support
wide metrics, which allows a 24-bit interface metric and a 32-bit path metric. However, Cisco IOS uses narrow metrics by default. Mixing routers using narrow and wide metrics would increase complexities. The
metric-style narrow,
metric-style wide, and
metric-style transition router subcommands instruct an IS-IS router to generate and accept old-style, new-style, and both styles of TLVs respectively.
Narrow- and wide-style metrics are not compatible with each other. Migration from narrow to wide metric is a 2-stage process using the
transition keyword. The
metric-style transition IS-IS router subcommand should first be configured on all routers that are using narrow metrics. Once the whole network support both old- and new-style TLVs, the wide-style metric can then be implemented using the
metric-style wide IS-IS router subcommand on all routers.
The metric defines the cost to a destination. ISO 10589 defined the following 4 types of metrics:
| Default | Also referred to as cost. Every Integrated IS-IS router must support this metric. The default cost applied to the outgoing interface of a Cisco router interface is 10. |
| Delay | An optional metric that reflects the transit delay. |
| Expense | An optional metric that reflects the monetary expense of the network. |
| Error | An optional metric that is based on the reliability of the path. |
Note: Optional metrics are chosen before the default metric; however, Cisco supports only the
default metric.
Another issue of the Cisco IS-IS implementation is that it does not scale the interface metric. All IS-IS interfaces have a default metric value of 10; however, this can be changed manually. If the default metric is not adjusted on each interface, the IS-IS metric becomes similar to the hop count metric of Routing Information Protocol (RIP).
Default IS-IS Path Metric Calculation
New ideas cannot be easily expressed as with OSPF, as they require the creation of a new LSA. The OSPF description schema is difficult to extend due to compatibility issues and it was developed exclusively for IPv4. IS-IS was designed with simplicity in mind, well-structured data formats, and can be easily extended through the Type, Length, and Value (TLV) mechanism. TLV triplets encode all IS-IS updates. This protocol-independence feature makes IS-IS easily extensible. IS-IS can easily grow to cover IPv6 (Integrated IS-ISv6) or any other new protocols, as extending IS-IS is simply creating new TLV triplets.
An organization might choose OSPF over IS-IS because OSPF is more optimized and was designed exclusively as an IP routing protocol. Besides that, it is relatively easy to find both networking equipments and personnel to implement and support an OSPF network infrastructure. Furthermore, OSPF documentation is much more readily available than IS-IS documentation.
Below summarizes the differences between OSPF and Integrated IS-IS:
| OSPF | Integrated IS-IS |
| Area border inside routers (ABRs) | Area border on links |
| Each link in only 1 area | Each router in only 1 area |
| Complex to extend the backbone | Simple to extend the backbone |
| Many small LSAs sent | Fewer LSPs sent |
| Runs on top of IP | Runs on top of data-link layer |
| Requires IP addresses | Requires IP and CLNS addresses |
| Default metric is scaled by interface bandwidth | Default metric is 10 for all interfaces |
| Not easy to extend | Highly extensible with new TLV triplets |
| Equipments, personnel, and documentation more readily available | Equipments, personnel, and documentation not as readily available |
IS-IS and OSPF have more similarities than differences.
Both routing protocols have the following characteristics:
- They are open standard link-state routing protocols that utilize the Dijkstra’s Shortest Path First (SPF) algorithm for their operations.
- They support VLSM and 2-level hierarchical routing.
- They have similar flooding mechanisms using link-state advertisements (LSAs), link-state aging timers, and link-state database synchronization to maintain the LSDB.
- They are successful in the largest and most-demanding deployments – ISP networks.
- They converge quickly upon network changes.
The development of IS-IS begun before OSPF development. Most of the development of the OSPF and IS-IS routing protocols was done concurrently. The cooperation and competition between the development groups produced 2 protocols that are very similar, yet one is better because of the other. The practical differences between the 2 protocols mainly deal with the issues of resources usage and customization.
Most debates of the merits of IS-IS and OSPF are colored by their mutual history – different groups with different cultures developed them.
IS-IS was originally developed by
Digital Equipment Corporation (DEC) for DECnet Phase V. In 1987, the ANSI chose it to be the OSI IGP. At that time it could route only CLNP. IS-IS’s evolution was ad-hoc; whereas OSPF was more formal. Below is a brief history of IS-IS:
- 1985 – Originally called DECnet Phase V Routing.
- 1988 – Adopted by ISO and renamed as IS-IS.
- 1990 – Publication of RFC 1142 – OSI IS-IS Intra-domain Routing Protocol.
- 1990 – Publication of RFC 1195 – Use of OSI IS-IS for Routing in TCP/IP and Dual Environments.
- 1991 – Cisco IOS Software starts supporting IS-IS.
- 1995 – Internet service providers (ISPs) start adopting IS-IS.
- 2000 – Publication of IETF draft – IS-IS Extensions for Traffic Engineering.
- 2001 – Publication of IETF draft – IS-IS Extensions in Support of Generalized MPLS.
IETF – Internet Engineering Task Force
The ISO process is an international standards development process. ISO and many other groups did not approve TCP/IP due to its origin – the US Department of Defense (DoD) protocol. From the perspective of ISO, the development of IP was chaotic and imprecise, based on the famous maxim of “loose consensus and running code”. From the perspective of the early Internet engineers, the ISO process was slow, irritating, and disenfranchising.
In 1988, the US National Science Foundation Network (NSFnet) was created. The IGP used was based on an early draft of IS-IS. The extensions to IS-IS for handling IP were developed in 1988. The development of OSPF just began during this time; OSPF was loosely based on IS-IS.
OSPF Version 1 (OSPFv1) was published in 1989, conflicts ensued between the supporters of IS-IS and OSPF. Eventually the IETF supported both, but with the unofficial endorsement of the IETF and its continued favor of OSPF, OSPF which provide native IP support became more popular eventually.
During the mid-1990s, large ISPs selected IS-IS as their IGPs for 2 reasons – IS-IS support IP and CLNS (solved 2 problems at once), and OSPF was still considered immature at the time.