Router#sh ip int fa1/0 FastEthernet1/0 is up, line protocol is up Internet address is 10.10.10.1/24 Broadcast address is 255.255.255.255 Address determined by setup command MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Outgoing access list is not set Inbound access list is not set Proxy ARP is enabled Local Proxy ARP is disabled --- output omitted ---
Local Proxy ARP is used when there is a need to perform proxy ARP for hosts in local network. Normally network devices do not perform local proxy ARP as they would assume the host with the requested IP address would answer the ARP request itself.
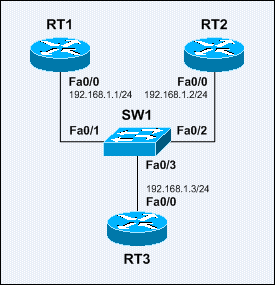
Sample Local Proxy ARP Network
The switchport protected interface subcommand is configured on SW1 Fa0/1 and Fa0/2.
The ip local-proxy-arp interface subcommand is configured on RT3 Fa0/0.
Below shows that RT3 is performing proxy ARP for RT2:
RT1#ping 192.168.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 17.0.0.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms RT1#sh arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.168.1.1 - 1111.1111.1111 ARPA FastEthernet0/0 Internet 192.168.1.2 6 3333.3333.3333 ARPA FastEthernet0/0 Internet 192.168.1.3 5 3333.3333.3333 ARPA FastEthernet0/0
The switchport protected interface subcommand configures a switch port as a protected port. Protected ports have the following characteristics:
1) A protected port does not forward any traffic (including unicast, multicast, and broadcast) to other protected ports – traffic cannot be forwarded between protected ports at Layer 2; all traffic between protected ports must be forwarded through a Layer 3 device.
2) Traffic between a protected port and a non-protected port is forwarded as usual.
Note: This feature applies upon a single switch, and cannot be extended across multiple switches.
Protected ports are being used in environments where traffic must not be forwarded between ports on the same switch so that an end system does not see the traffic from another end system. Below are some other sample usages of protected ports:
1) A hotel environment where the ports for each room should not be able to communicate with each other, but they need to communicate with the gateway.
2) A DMZ zone where the ports for each server should not be able to communicate with each other in order to prevent further damages of other servers when a server is owned.
3) A collocation environment where servers from different customers should not be able to communicate with each other.
No comments:
Post a Comment