When using an extended access list for a route map, it acts like a prefix list, which means that it can match both the address and subnet masks of IP prefixes. IP prefixes of 10.0.0.0/8 and 10.0.0.0/16 can be differentiated by defining that the address must be 10.0.0.0 and the subnet mask must be /8. The syntax of prefix list to achieve this is very straightforward as below:
ip prefix-list prefix-test01 permit 10.0.0.0/8
The extended access lists to achieve the same result as the prefix list above are as below. Note that the extended access lists are no longer matching any source and destination address pairs, but instead matching the address and subnet mask – this means that the address must be exactly 10.0.0.0 and the subnet mask must be exactly 255.0.0.0.
access-list 101 permit ip host 10.0.0.0 host 255.0.0.0
--- OR ---
access-list 101 permit ip 10.0.0.0 0.255.255.255 host 255.0.0.0
Note: The standard access list to achieve the similar result is:access-list 1 permit 10.0.0.0 0.255.255.255
The extended access list above can perform fuzzy binary matches by changing the host keyword to a wildcard mask. The configuration below matches any address that starts with 192.168. and has a subnet mask of /24, which matches 192.168.0.0/24, 192.168.100.0/24, etc.
access-list 102 permit ip 192.168.0.0 0.0.255.255 host 255.255.255.0The source address part of the access list matches the destination address of the route; while the destination address part of the access list – the network mask in fact, indicates the range.
The confusion lies upon when extended access lists are being referred by distribute lists. The source and destination fields in the extended ACL syntax match the update source of the route and the network address respectively. This provides the mechanism to control which networks are being received, and more importantly from whom the networks were received from.
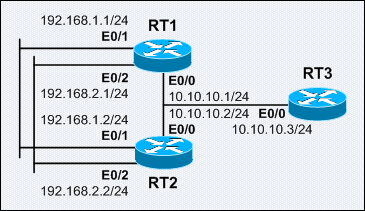
Below shows that RT3 learned the 2 prefixes twice, once from RT1 and once from RT2.
RT3#sh ip route rip
R 192.168.1.0/24 [120/1] via 10.10.10.1, 00:00:02, Ethernet0/0
[120/1] via 10.10.10.2, 00:00:20, Ethernet0/0
R 192.168.2.0/24 [120/1] via 10.10.10.1, 00:00:02, Ethernet0/0
[120/1] via 10.10.10.2, 00:00:20, Ethernet0/0
RT3#
Below implement an extended access list along with the distribute list on RT3 to only receive the 192.168.1.0/24 and 192.168.2.0/24 prefixes from RT1 and RT2 respectively.
RT3#conf t Enter configuration commands, one per line. End with CNTL/Z. RT3(config)#access-list 101 permit ip host 10.10.10.1 host 192.168.1.0 RT3(config)#access-list 101 permit ip host 10.10.10.2 host 192.168.2.0 RT3(config)# RT3(config)#router rip RT3(config-router)#distribute-list 101 in Ethernet0/0 RT3(config-router)#end RT3# RT3#clear ip route * RT3#sh ip route rip R 192.168.1.0/24 [120/1] via 10.10.10.1, 00:00:01, Ethernet0/0 R 192.168.2.0/24 [120/1] via 10.10.10.2, 00:00:02, Ethernet0/0 RT3#
Now that RT3 has only one entry for each prefix, with 192.168.1.0/24 coming only from RT1 and 192.168.2.0/24 coming only from RT2. The disadvantage on this configuration is that it is unable to differentiate prefixes based on their subnet masks, eg: unable to control to receive only 172.16.0.0/16 from RT1 and 172.16.0.0/24 from RT2. Prefix list along with distribute list should be implemented using the distribute-list prefix {ip-prefix-name} router subcommand to achieve such requirement.
Below shows some other examples of prefix lists and their equivalent extended access lists.
Ex #1: Matches only the 172.16.10.0/24 prefix.
= ip prefix-list prefix-test01 permit 172.16.10.0/24
= access-list 101 permit host 172.16.0.0 host 255.255.255.0
Ex #2: Matches subnets from 172.16.0.0/16; the entire class B range.
= ip prefix-list prefix-test01 permit 172.16.0.0/16 le 32
= access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.0.0 0.0.255.255
Ex #3: Matches subnets from 172.16.0.0/16 with a prefix length between /24 and /32.
= ip prefix-list prefix-test01 permit 172.16.0.0/16 ge 24
= access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.255.0 0.0.0.255
Ex #4: Matches subnets from 172.16.0.0/16 with a prefix length between /24 and /30.
= ip prefix-list prefix-test01 permit 172.16.0.0/16 ge 24 le 30
= access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.255.0 0.0.0.252
(NOT) access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.255.3 0.0.0.252
What if you have "distribute-list route-map XXX in"
ReplyDeleteWill it act like a route-map or a distribute-list?