802.1X allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the switch port which an unauthenticated client is connected to. Normal traffic can pass through the switch port after authentication is completed successfully.
With 802.1X port-based authentication, network devices have the following device roles:
| Client (Supplicant) | The device (workstation) that requires access to the LAN. Responds to the requests from the switch. Must be running 802.1X-compliant client software. |
| Switch or Access Point (Authenticator) | Controls the physical access to the network based on the authentication status of the client. Acts as a proxy between the client and authentication server, which requests identity information from the client, verify the information with the authentication server, and relays the response to the client. It is responsible for the re-encapsulation of the EAP and RADIUS frames for communication with a client and an authentication server respectively. |
| Authentication Server | Performs the authentication of the client. It validates the identity of the client and notifies the switch or access point whether the client is authorized to access the network. Currently, the RADIUS security system with EAP extensions is the only supported authentication server. |
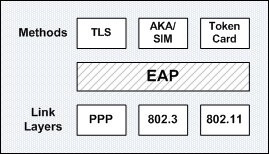
The EAP Architecture
EAP is designed to run over any link layer and use any number of authentication methods.
IEEE 802.1X Authentication Message Exchange
Below describes a typical WLAN 802.1X authentication process:
1) A wireless client becomes active on the medium. After the IEEE 802.11 WLAN Probe Request/Response, Authentication, and Association processes, the access point forces the port into an unauthorized state, which only 802.1X traffic is forwarded.
2) The access point replies with an EAP-Request Identity message to the wireless client to obtain the client’s identity. The wireless client’s EAP-Response Identity message, which contains the client’s identity, is forwarded to the authentication server.
3) The authentication server authenticates the wireless client and sends an Access Accept (or Access Reject) message to the access point.
4) Upon receiving the Access Accept message, the access point relays the EAP-Success message to the wireless client and transitions the client’s port to an authorized state and normal traffic is forwarded.
Note: Below lists the sequence of establishing WLAN connectivity with 802.1X authentication:
Probe Request, Probe Response, Authentication, Association, 802.1X authentication…
When 802.1X is enabled, ports are authenticated before any other L2 or L3 features are enabled.
Note: 802.1X is also considered as an efficient and effective alternative solution to port security.

Hi Yap,
ReplyDeletecongratulations for your blog. I am currently preparing to renew my CCNP certification with exam SECURE and your post are being very helpful.
Greetings from Madrid and thank you very much
hi there, thanks for dropping a comment and enjoy your stay here. :-)
ReplyDelete