VPNs are secure and inexpensive. There are 2 types of VPN implementation – using IPsec to create authentication and encryption services; and establishing tunnels via tunneling protocols.
Tunneling is method of overcoming protocol restrictions by encapsulating or wrapping packets from a protocol in another protocol and transmits the encapsulated packet over a network that supports the encapsulating protocol.
Below describes the most common tunneling protocols:
| Layer 2 Forwarding (L2F) | A Cisco-proprietary tunneling protocol created for Virtual Private Dial-Up Networks (VPDNs), where devices create secure connections to a corporate network using dial-up connections. L2F was later replaced by L2TP (backward compatible with L2F). |
| Point-to-Point Tunneling Protocol (PPTP) | Created by Microsoft for secure data transmission between remote networks and corporate network. |
| Layer 2 Tunneling Protocol (L2TP) | Created by Cisco and Microsoft to replace L2F and PPTP. L2TP merged both L2F and PPTP capabilities into one tunneling protocol. |
| Generic Routing Encapsulation (GRE) | Another Cisco-proprietary tunneling protocol. It forms (unencrypted) virtual point-to-point links which are able to encapsulate a variety of protocols inside IP packets. It can also be used to protect the private address space from being advertised to any public domain. |
IPsec is a suite of industry standard network layer (L3) protocols and algorithms for securing communications over the IP-based networks by authenticating and/or encrypting IP packets. IPsec also includes the IKE protocol for establishing shared security information (Security Association, SA) between 2 network devices or end systems to support secure communication.
Note: Other Internet security protocols, eg: SSL and SSH, are operate from the Transport layer up to the Application layer (L4 – L7).
Note: The official term of “IPsec” as defined by the IETF is often wrongly addressed as “IPSec”.
IPsec secures a path between a pair of gateways, a pair of hosts, or a gateway and a host.
IPsec unable to encrypt non-IP traffic. For such a situation, a GRE tunnel would first be created to encrypt the non-IP traffic and followed by using IPsec to encrypt the GRE tunnel. Additionally, Multicast can only be passed on GRE tunnels.
IPsec-based VPN is comprised of 2 parts – Internet Key Exchange (IKE) protocol and IPsec security protocols – Authentication Header (AH) and Encapsulating Security Payload (ESP). Below describes the flow of IPsec events:
i) IKE Phase 1: IKE Security Negotiation – IKE negotiates how to protect IKE by establishing an authenticated and secure channel between 2 IKE peers called the IKE Security Association. IKE Phase 1 is consists of Main Mode or Aggressive Mode. The peer that initiates the session will propose or offer at least one or more configured ISAKMP policies which specify a combination of encryption algorithm, hash algorithm, authentication type, Diffie-Hellman group, and the lifetime. The remote peer will then try to find a matching configured policy that has the same parameters as the one being sent by its peer. If no matching policy is found, IKE will terminate the negotiation. If a policy is mutually agreed upon, IKE will complete the negotiation process and an ISAKMP SA will be created. Additionally, peers in an IPsec session must authenticate themselves among each other during IKE Phase 1 Main Mode exchange before IKE can proceed.
ii) IKE Phase 2: IPsec Security Negotiation – IKE negotiates how to protect IPsec by negotiating the IPsec security associations (SAs) and generating the keys for IPsec. IKE Phase 2 negotiation is done in only 1 mode – Quick Mode. The peer that initiates the session will propose or offer at least one or more configured transforms which specify a combination of authentication and/or encryption algorithm. The remote peer will then try to find a matching configured transform that has the same parameters as the one being sent by its peer. If no matching transform is found, IKE will terminate negotiation and an IPsec VPN will not be established. If a policy is mutually agreed upon, IKE will complete the negotiation process and an IPsec SA will be created.
iii) IPsec transfers the actual data in the VPN tunnel using the authentication and encryption methods agreed upon the IKE negotiation process.
Internet Key Exchange (IKE) allows 2 VPN endpoints verify the identity of each other (using pre-shared keys or RSA) in IKE Phase 1, and negotiate the methods (security policies) for secured data transmission in IKE Phase 2. IKE manages VPN connections by defining a set of Security Associations (SAs) for each connection. Each SA has its own SAID.
In a VPN, before a communication path is considered secure, the VPN endpoints must be authenticated. IPsec uses the following authentication methods to authenticate peers:
| Pre-Shared Keys | Secret key values that are manually configured on each peer. |
| RSA signatures | Use the exchange of digital certificates to authenticate the peers. |
IKE is a hybrid protocol that uses part of Oakley and part of SKEME inside the ISAKMP framework; hence IKE is formerly known as ISAKMP/Oakley. IKE typically uses ISAKMP for key exchange and establishment of SAs, although other methods can be used.
IKE establishes both ISAKMP and IPsec SAs for an IPsec VPN session. IKE first negotiates an ISAKMP SA with the peer. It is possible to configure multiple policy statements with different parameters, and then allow the peers to negotiate and establish a mutual agreement.
An IPsec SA defines the security algorithms or parameters associated with particular connection – the IPsec protocol (AH, ESP, or both), the session keys used for data encryption, etc. IPsec SAs are unidirectional (simplex); hence there is always more than 1 IPsec SA per IPsec connection. In cases where only either AH or ESP is used, 2 SAs will be created for each connection – one for each the incoming and outgoing traffic. In cases where AH and ESP are used in conjunction, 4 SAs will be created.
The Internet Security Association and Key Management Protocol (ISAKMP) defines the procedures for authenticating peers, IKASAMP and IPsec SAs establishment, negotiation, modification, and deletion; key generation, and threat mitigation (eg: DoS and replay attacks).
Instead of ISAKMP (the use of ipsec-isakmp keyword along with the crypto map global configuration command), manual keying (the use of ipsec-manual keyword along with the crypto map global configuration command) which require manual entry of the shared secret session keys (used for hashing and encryption) on both crypto endpoints is also possible.
IPsec operation requires both ends to be configured with the same transform set, which specifies the methods for encrypt and decrypt the data. IPsec uses 2 primary security protocols – Authentication Header (AH) and Encapsulating Security Payload (ESP). These protocols are used for secured data transmission through an IPsec-based VPN tunnel. IPsec-based VPNs can be established using AH only, ESP only, or both AH and ESP.
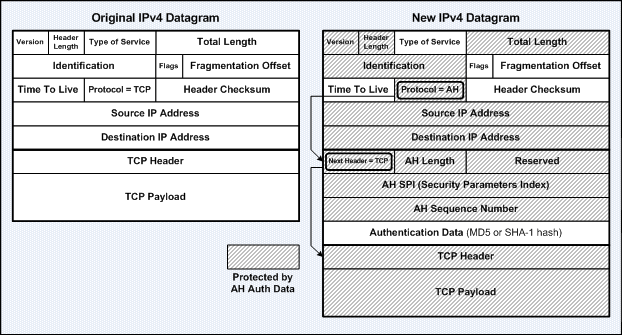
The Authentication Header (AH) protocol provides authentication for both the IP header and data of a packet using a one-way hash function. The sender first generates a one-way hash, and then the receiver generates the same one-way hash. If the packet has changed in any way, it won’t be authenticated and will be dropped. IPsec relies upon AH to guarantee authenticity. AH provides integrity check on the entire packet, but it doesn’t provide any encryption services.
ESP only provides integrity check (and encrypts) on the data of a packet (and the ESP header); while AH checks the entire packet – both header and data. AH is used for authentication only, while ESP can be used for either encryption or authentication only; or both.
Although AH and ESP are typically used independently, they are often being used together to provide data encryption service. Note: It is important to use authentication even if encryption is used, as encrypt-only implementations are subject to some forms of effective attacks.
ESP provides the following 4 functionalities or capabilities:
| Confidentiality (Encryption) | Provided through the use of symmetric encryption algorithms, eg: DES, 3DES. Confidentiality can be selected separately from all other services, but the confidentiality selected must be the same on all VPN endpoints. |
| Data Origin Authentication and Connectionless Integrity | Joint services offered as an option in conjunction with the confidentiality option. Authentication ensures that the connection is established with the desired system. |
| Anti-Replay Protection | This service works only if data origin authentication is selected. It is based upon the receiver – it is effective only if the receiver checks the sequence number of the received packets with a sliding window of the destination gateway or host to prevent replay attacks. |
| Traffic Flow Confidentiality | This service works only when tunnel mode is selected. It is most effective if implemented at a security gateway, where the source-destination patterns of attacks is visible. |
The degree of security of IPsec VPN is based on the encryption algorithm used and the length of the pre-shared key. The longer the key, the harder it is to be broken.
IPsec is not bound to any specific encryption or authentication algorithm, keying or technology, or security algorithms, which allows IPsec to support newer and better algorithms.
IPsec supports the following 3 types of encryption algorithms:
| Data Encryption Standard (DES) | Uses a 56-bit key that ensures high performance encryption. Uses a symmetric key cryptosystem. |
| Triple DES (3DES) | A variant of DES that breaks data into 64-bit blocks. 3DES then processes each block 3 times, each time with an independent 56-bit key, hence providing significant improvement in encryption strength over DES. Uses a symmetric key cryptosystem. |
| Advanced Encryption Standard (AES) | Provides stronger encryption than DES and is more efficient than 3DES. Key lengths can be 128-, 192-, and 256-bit keys. |
Encryption algorithms (eg: DES, 3DES, and AES) require a symmetric shared secret key to perform encryption and decryption. The Diffie-Hellman Key Exchange (D-H) is a public key exchange process that allows 2 parties that have no prior knowledge of each other to negotiate symmetric shared secret keys used for encryption and decryption over an insecure channel. The shared secret keys are negotiated between crypto endpoints dynamically, which only the prime modulus size for use in the D-H exchange is needed to be specified. IKE uses the D-H keys to encrypt the ISAKMP SA when establishing the IPsec SAs. Additionally, D-H is also used to generate shared secret keys to be used in the ciphers specified in the IPsec transforms, which are then used in conjunction with the D-H keys by the IPsec to encrypt and decrypt the data passes through the IPsec VPN tunnel.
IPsec uses a data integrity algorithm called Hash-based Message Authentication Code (HMAC) that adds a hash to the message to ensure data integrity. The hash guarantees the integrity of the original message. If the transmitted hash matches the received hash, the message is considered has not been tampered.
IPsec uses the following 2 HMAC algorithms:
| Message Digest Algorithm 5 (MD5) | Uses a 128-bit shared secret key. The message and 128-bit shared secret key are combined and run through the MD5 hash algorithm, producing a 128-bit hash. This hash is then added to the original message and sent to the destination host. |
| Secure Hash Algorithm 1 (SHA-1) | Uses a 160-bit shared secret key. The message and 160-bit shared secret key are combined and run through the SHA-1 hash algorithm, producing a 160-bit hash. This hash is then added to the original message and sent to the destination host. |
Below lists the 2 modes of IPsec operation:
| Transport | Only the payload of the IP packet is encrypted and/or authenticated. The routing is intact, as the IP header is neither modified nor encrypted. It is used for host-to-host or end-to-end communications (end systems perform the security processing). |
| Tunnel | The entire IP packet is encrypted and/or authenticated. The original packet is encapsulated entirely into a new packet with a new set of source and destination IP addresses for routing to work. It is used for network-to-network or portal-to-portal communications (gateways or routers perform the security processing). It is the traditional and default mode of IPsec VPNs. |
The Tunnel mode is most commonly used to secure existing IP traffic for communication between end systems on networks connected to IPsec-enabled routers. With routers or VPN endpoints performing the IPsec encryption, no changes are required to the software and drivers on the end systems – the IPsec implementation is transparent to end systems.
IPsec in AH Transport Mode
IPsec in AH Tunnel Mode
IPsec in ESP Transport Mode
IPsec in ESP Tunnel Mode
The main challenge and problem faced by IKE and IPsec is NAT, as both protocols were not designed to work through NAT. NAT Traversal (NAT-T) has evolved as a method of enabling IPsec-protected IP packets to work well in NAT environments by encapsulating ISAKMP and ESP packets into UDP Port 4500 packets.
The IPsec NAT Transparency feature was introduced in Cisco IOS Release 12.2T.
The access control list configuration named UDP Port 4500 as “non500-isakmp”. :-)



It proved to be Very helpful to me and I am sure to all the commentators here! online
ReplyDeleteI am unable to read articles online very often, but I’m glad I did today. This is very well written and your points are well-expressed. Please, don’t ever stop writing. TutuApp iOS 11
ReplyDeleteGood website! I truly love how it is easy on my eyes it is. I am wondering how I might be notified whenever a new post has been made. I have subscribed to your RSS which may do the trick? Have a great day! AppEven
ReplyDeleteNice post. I was checking constantly this blog and I am impressed! Extremely helpful information specially the last part I care for such info a lot. I was seeking this particular information for a very long time. Thank you and good luck. appvn
ReplyDeleteHowever, with various choices to look over,https://novavpn.com/blog/popcorn-time/ how would you choose the best VPN benefit?
ReplyDeleteteen patti gold apk
ReplyDeleteteen patti gold apk hack
omegle alternative apps
best apps like omegle
best text chat sites
omegle alternative text sites
download play store pro apk free
download play store pro free apk
download play store pro apk free
download free play store pro
Best Nursing Diagnosis
ReplyDeleteBest Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Best Nursing Diagnosis
Much obliged to you for peopling get the data they require. Extraordinary stuff of course. Keep up the colossal work!!! visit website
ReplyDeleteI wish more authors of this type of content would take the time you did to research and write so well. I am very impressed with your vision and insight. https://prywatnoscwsieci.pl
ReplyDeleteWow this was amazing. I was just about to look for some expert and educative content like this, I am grateful that I have frequented here! privatnost online
ReplyDeleteI would like to thank you for the efforts you have made in writing this article. I am hoping the same best work from you in the future as well. In fact your creative writing abilities has inspired me to start my own BlogEngine blog now. Really the blogging is spreading its wings rapidly. Your write up is a fine example of it. www.lemigliorivpn.com
ReplyDeleteJust admiring your work and wondering how you managed this blog so well. It’s so remarkable that I can't afford to not go through this valuable information whenever I surf the internet! https://gizlilikveguvenlik.com
ReplyDeleteIt is an excellent documents, simple to read and combined all the aspects together. !!!!!!Appreciate!!!!!! andy michael
ReplyDeleteI know your aptitude on this. I should say we ought to have an online discourse on this. Composing just remarks will close the talk straight away! What's more, will confine the advantages from this data. privacidadenlared
ReplyDeleteNothing compares to Weber using Genesis sort of grills. That is certainly the type gas grills which have been that will always make sure that they deliver a high performance part of down interval https://diadiktiokaiasfalia.com
ReplyDeleteAssume paid for with the help of center, have discovered modern society; believed that protect on your playlists, you could potentially know most of the hassle; assumed ones step quit, much more is unable to drive; Imagine I would like adore, merely the caress. internetprivatsphare.ch
ReplyDeleteGreat post yet I was thinking about whether you could compose a litte more on this subject? I"d be exceptionally grateful in the event that you could expound a tad bit further. Value it! lesmeilleurs vpn
ReplyDeleteA portable fish finder has other benefits too. They are light-weight and simple to use. Plus they let you use a fish finder in eventualities where you will not be able to employ a fixed one. vpn austria
ReplyDeleteI real glad to uncover this web internet site on bing, just what I was searching for. Netflix VPN
ReplyDeleteYou don't need only a portable VPN supplier; you need somebody who can protect all your different associations also.
ReplyDeletehttps://www.router-reset.com/how-flush-dns-cache/
It was thinking about whether I could utilize this review on my other site, I will connect it back to your site though.Great Thanks. vpn veteran
ReplyDeleteTutuapp
ReplyDeleteTutuapp Download
Tutuapp
Tutuapp apk
Appvn Apk
ReplyDeleteAppvn ios
Blackmart Apk
iTube Apk
Snaptube iOS
Snaptube Apk
The element which makes this blog unique is the optimism seen throughout.
ReplyDeleteget VPN
This comment has been removed by the author.
ReplyDeleteMany homework on the continual hunt along with offstage on the road to winning. Definitely not attached, simple to-fall as a result of wayside; And not investigation, afterward into a path travel toward the black. allertaprivacy
ReplyDeleteA debt of gratitude is in order for offering this quality data to us. I truly delighted in perusing. Will without a doubt going to impart this URL to my companions. vpnveteran.com
ReplyDeleteOrganizations can outfit the information of its workers by recording and facilitating it on the intranet. gizlilikveguvenlik.com
ReplyDeleteYour blog provided us with valuable information to work with. Each & every tips of your post are awesome. Thanks a lot for sharing. Keep blogging deze website
ReplyDeleteI genuinely believed you would probably have something useful to say. All I hear is a bunch of whining about something that you can fix if you were not too busy looking for attention. After all, I know it was my choice to read.. internetet securite website
ReplyDeleteOn the off chance that you have not known about the word VPN, VPN implies Virtual Private Network. It for the most part concerns a lot of work stations arranged together over the web. Buy VPN Account With Monero
ReplyDeletefashion for women
ReplyDeleteonline shopping
blog provided us with valuable information to work with. Each & every tips of your post are awesome. Thanks a lot for sharing. Keep blogging edtechwiki.org
ReplyDeleteThanks for the blog post buddy! Keep them coming... nord vpn free trial
ReplyDeleteI am definitely enjoying your website. You definitely have some great insight and great stories. windscribe free
ReplyDeleteThank you for the update, very nice site.. tor vs vpn
ReplyDeleteThank you very much for this useful article. I like it. avast vpn torrenting
ReplyDeleteIn past hosting plans there is a significant issue of traffic taking care of at whatever point there is an ascent in rush hour gridlock, different servers can't deal with it on account of restricted data transfer capacity. Your server gets over-burden and smashed.windows
ReplyDeleteVPS Hosting enables organizations just as people to exploit it by offering different administrations.VPS Servers
ReplyDelete
ReplyDeleteTutu Helper is the one of the best ios,android App store to get the tons of free app and game. Here the latest version of TutuApp of free.
Tutu Helper Apk
TutuApp free
tutuapp pokemon go
ReplyDeleteWhatsapp plus is one of the best mod app for official whatsapp for free, get unlimited features of
whatsapp plus for free. Here Click to download the latest version whatsapp plus apk.
WhatsApp Plus
Download WhatsApp Plus
Awesome blog. I enjoyed reading your articles.
ReplyDeleteFantastical Crack
Thank you so much for sharing this information with everyone who knows what you are talking about! Compile.
ReplyDeletemovavi video converter
iphone backup extractor
dvdfab crack
manycam pro crack
I really liked your article.Much thanks again. Really Great.
ReplyDeletetoon boom harmony premium serial key
automatic email manager
bulk image downloader crack
I like the result, I found what I wanted and you finished the 4-day hunt!
ReplyDeleteMay God give your husband health and I wish you a happy day.
refx nexus crack
This is really nice and useful information. I am
ReplyDeleteI am glad that you have shared this useful information with us.
So, keep us posted. Thanks for sharing.
all in one toolbox pro apk crack
spyhunter crack
nitro pro crack
deep freeze crack
macrium reflect crack
nitro pro free download with crack
I like the result, I found what I wanted, and you completed a 4-day hunt!
ReplyDeleteGod bless your husband and wish you a happy day. day
mountain duck crack
coreldraw x
macrium reflect with crack
quarkxpress v15 2 1 crack
After looking over a number of the blog posts on your
ReplyDeletethe site beutiful post this is good working of site
wirecast pro crack
minitool power data recovery crack
driver booster pro crack
https://iqbalpc.com/mendeley-crack/
ReplyDeletehttps://iqbalpc.com/
Such an amazing article. This is very knowledgeable and understandable article. Thanks for sharing it with us.
Yuk Gabung di NAGAQQ: AGEN BANDARQ BANDARQ ONLINE ADUQ ONLINE DOMINOQQ TERBAIK
ReplyDeleteYang Merupakan Agen Bandarq, Domino 99, Dan Bandar Poker Online Terpercaya di asia hadir untuk anda semua dengan permainan permainan menarik dan bonus menarik untuk anda semua
Bonus yang diberikan NagaQQ :
* Bonus rollingan 0.5%,setiap senin di bagikannya
* Bonus Refferal 10% + 10%,seumur hidup
* Bonus Jackpot, yang dapat anda dapatkan dengan mudah
* Minimal Depo 15.000
* Minimal WD 20.000
Games Yang di Hadirkan NagaQQ :
* Poker Online
* BandarQ
* Domino99
* Bandar Poker
* Bandar66
* Sakong
* Capsa Susun
* AduQ
* Perang Bacarrat
* Perang Dadu
* BD QQ (New Game)
Menyediakan deposit Via E-Money
Seperti : OVO, Dana , Gopay, Link aja ,dll
Info Lebih lanjut Kunjungi :
Website : NagaQQ
Facebook : NagaQQ Official
Kontakk : Info NagaQQ
linktree : Agen Judi Online
WHATSAPP 1 : +855977509035
Line : Cs_nagaQQ
TELEGRAM : +855967014811
BACA JUGA BLOGSPORT KAMI YANG LAIN:
agen bandarq terbaik
Winner NagaQQ
Daftar NagaQQ
Agen Poker Online
hello!
ReplyDeleteI really adore your writing!
I love your writing! Share we convey your post on AOL in addition?
I need a home specialist to handle my situation.
Perhaps that's you! I'm looking forward to seeing you.
live2d cubism pro crack
ms office 2016 crack
ReplyDeleteVery good blogspot, Also I love this article.
wise care 365 pro crack
pinnacle studio ultimate crack
manageengine desktop central crack
total commander crack
However, what about the last sentence? Are you sure of the origin?
ReplyDeleteHello friends, your wonderful article on the subject of learning and well explained, keep up the good work. Hello friends a good and offensive note is mentioned here for me
I love it. Surprised, I have to admit. Rarely do I find a blog that is similarly informative and entertaining, and
Sure enough you hit a nail in the head. I found your blog site on Yahoo and looked at your first post
content. Keep it running smoothly.
novapdf pro crack
avs video converter crack
inpixio photo cutter crack
filelocator pro crack
ReplyDeleteHowdy! This is my 1st comment here so I just wanted to give a
quick shout out and tell you I truly enjoy reading through your posts.
Can you suggest any other blogs/websites/forums that go over the same topics?
Thanks a ton!
adobe character animator cc crack
reaper crack
on1 portrait ai crack
arclab dir2html crack